Encrypted DNS and SNI Make Pirate Site Blocking Much Harder

The practice has been around for well over a decade and has gradually expanded to dozens of countries around the world.
The actual blocking is done by Internet providers, often following a court order. These measures can range from simple DNS blocks to more elaborate schemes involving Server Name Indication (SNI) eavesdropping, or a combination of both.
Thus far, the more thorough blocking efforts have worked relatively well. However, there’s a growing concern among network specialists that blocking and filtering could become problematic in the future as technology moves forward.
For example, tech companies are increasingly starting to adopt DNS over HTTPS (DoH or encrypted DNS). This makes it possible to resolve domain names over the secure HTTPS protocol. As a result, it’s harder for outsiders, including ISPs, to eavesdrop on which sites people access.
Earlier this year, BT’s Principal Network Architect, Andy Fidler, warned that encrypted DNS is a potential game changer in the area. In a presentation before several industry specialists, he outlined a variety of concerns, as ITPro notes.
Among other things, these new developments will make it harder to block websites and to comply with court orders.
“If UK ISPs are no longer in the DNS path, they may not be able to fulfil certain domain specific court order blocking requests,” Fidler notes in his presentation.
“DNS blocking is the most granular tool in the kit box used by UK ISPs to implement Government / Regulation blocking orders,” he adds.
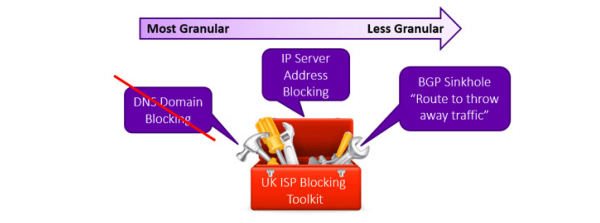
With regular DNS queries, ISPs such as BT can see which websites users are trying to access, even when people are using a third-party DNS provider. When DNS queries are encrypted, however, Internet providers can no longer see which websites customers visit.
BT’s Principal Network Architect called on UK Internet providers and the broader industry to see how they can respond to these developments. While increased privacy for users is not a bad thing, ineffective website blockades, useless parental filters, and other issues are seen as problematic.
This stance was also reiterated previously by a spokesperson for the UK’s Internet Services Providers’ Association, who informed Forbes that encrypted DNS should not break existing protections.
“If internet browser manufacturers switch on DNS encryption by default, they will put users at serious risk by allowing harmful online content to go unchecked.
“We would expect Internet browsers to provide the same protections, uphold the same standards and follow the same laws as U.K. ISPs currently do,” the association’s spokesperson added.
Advancements like this will be hard to stop though. Cloudflare already offers encrypted DNS through its 1.1.1.1 nameserver and Firefox has enabled support for encrypted lookups since Version 62.
And there’s more trouble on the horizon.
While encrypted DNS will make it harder for ISPs to block sites, it will certainly not be impossible. SNI eavesdropping is still an option, for example.
This may no longer be as easy in the future either. In tandem with increased support for encrypted DNS, more tech companies are embracing encrypted SNI as well, which prevents ISPs from snooping on SNI handshakes.
Last September, Cloudflare announced that encrypted SNI was live across Cloudflare’s network and a few weeks later, Mozilla followed suit by adding support for ESNI to its Firefox browser.
This combination of encrypted DNS and SNI makes it very hard for ISPs to prevent access to pirate sites. Providers can still use blunt tools such as IP-address blocking, but that could become troublesome when sites move to shared IP-addresses.
While this sounds problematic for site blocking efforts worldwide, it’s not a major issue just yet. Support from browsers and network providers is still limited, and site owners don’t appear to see this as a priority either.
The effectiveness will, of course, rely on which blocking methods an ISP uses, but on the more aggressive ones, a lot of boxes have to be ticked in order to effectively bypass a thorough website blockade.
For example, when we try to bypass the Pirate Bay blockade with both encrypted DNS and SNI, as well as support for DNSSEC and TLS 1.3, it still doesn’t work. Perhaps the ISP simply nullrouted the path to TPB in our case, as a trace suggests.
It’s also worth pointing out that, although The Pirate Bay uses Cloudflare’s compatible network, the domain doesn’t support DNSSEC, which is a potential vulnerability.
That said, it is still early days, and it wouldn’t be a surprise to see site operators and users fiddling around with this in the future. Meanwhile, other blocking-busters such as VPNs and the Tor browser remain an option as well.
Update: we clarified the text to add that in our test TPB was likely nullrouted.
Source: TF, for the latest info on copyright, file-sharing, torrent sites and more. We also have VPN reviews, discounts, offers and coupons.




Leave a Reply
Want to join the discussion?Feel free to contribute!